IAME Decentralized System Identification Network built for Blockchain Ecosystem.
IAME is a professional system for that will enable Blockchain identify verification by parties who are involved in executing transactions on Blockchain platform to confirm it’s identify at any level whether primary or secondary. It is built specifically to serve peer -2- peer exchanges in Blockchain.
Challenge in the present identification system
- Is dependent on individual sharing their own data and backing up
evidence with counterparties keeping in mind the end goal to distinguish
themselves and well –spring of riches.
The counterparties or other individual involved in the transaction holds the mutual information entirely.
This makes it easy for identification of a person and their source or well spring of riches.
More transaction on such platform, more powerlessness to the information shared.
The more information a person submits, the more extreme the consequences in security identification breach.
Solution by IAME that will change identification processes: - Fragmentation of individual’s data preceding confirmation by a progression of third parties who does not belong to any group within the exchange. Once this is achieved, it would sidestep the requirement for any value-based counterparty from processing or storing information.
- This process is powered by IAM digital token.
- In a regular system, the first step is to accepts or agree to a request by a counterparty to identify himself, so that the counterparty may find out to a level with whom she or he is executing the transaction with and by doing this, excess personal information is given out, before even realizing the damage it may cause.
- IAME platform on the other hand is that the same information that is supposed to be submitted in full will now be shared into little meaningless fragments, in a way that even if they are merged, it will not form any useful data.
- Also in the traditional for instance, a given string may be Bill
Gate, from Nigeria, if this is given in whole as it were, it means the
name Bill Gate can easily be sorted out. On the contrary, IAME system
will shard the name into tiny useless string in this format below:
For string type Bill;
Fragment A = B
Fragment B = il
Fragment C = lb.
By this, the wholesome data is in shreds.
THE NETWORK:
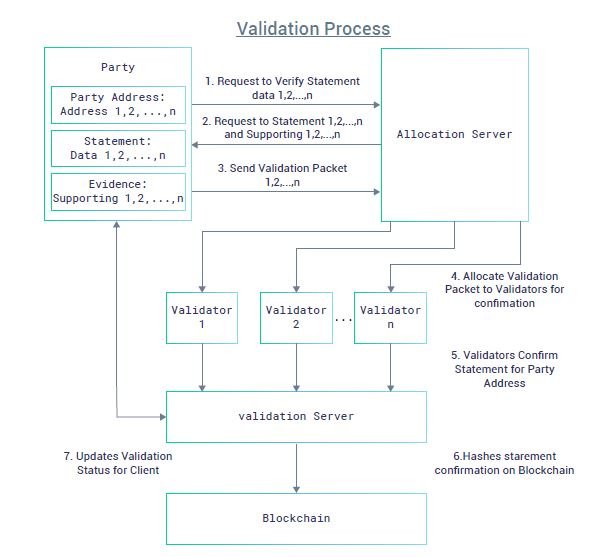
IAME network consists of 5 components
- Client component
- Allocation server
- Validation server
- Writeable Blockchain
- Identity server
These components are summed up in two major components – validation and identity server as shown in the diagram below:
IAM TOKEN: Like any other Blockchain platform, either coin or token as it may be called, is needed for transactions at different level. To this effect, IAME introduces IAM token to enable users gain access maximally during confirmation requests especially for packets authentication. This token will be used as a reward to include third party validators in the implementation stages. Thus the distribution of IAM token is dependent on the decision of the tribunal (more details refer to https://iame.io/res/180301-IAME-White-Paper-en.pdf)
Conclusion: The amount of information you share are the personal data you share with a counterparties. Insecurity is in the present system and I order to guide against being a victim of shared information, you need to join IAME platform. Be that as it may, in an economy where the quantity of electronic exchanges a man conducts is always expanding, the quantity of purposes of potential vulnerabilities increment exponentially, diminishing any favorable position picked up from security developments.
Road Map
From the bootstrapped basement project to full start up, IAME has come a long way.
On the road to ICO, we have honed our claws against angel investors to come up with a viable strategy and secure the funds necessary to begin development.
With confidence that we will launch our ICO, and we can say with certainty that we will bring the IAME project to a great end result.
Identifying Icon Identification
Identification:
Any information you share makes you vulnerable to theft and any information you collect makes you vulnerable to litigation. What’s the best way to solve this?
Validate Icon Validation
VALIDATION:
Every piece of information you share makes you vulnerable, and any information you collect makes you vulnerable to litigation. Do not share, do not take.
press

Team
A team of amazing ordinary people who want to know naturally and always strive to achieve the best to deliver the best possible results to the highest standards.

Nathaniel Tsang Mang Kin
Co-founder / Compliance

Suryani Chang
Co-founder / Back End

Chirag Patel
Front

Ari Vivekanandarajah
Community manager

Ludovik Lejeune
Front

Kevin Chung-Fat
Back End

Stephen Sunassee
Desainer UI
Counselor







Conclusion
The amount of information you share is personal data you share with a partner. Insecurity exists in the current system and I am instructing to guide not to be a victim of shared information, you need to join the IAME platform. Nevertheless, in an economy in which the number of electronic exchanges by a man is always widespread, the quantity of objectives of the potential exponential vulnerability increases, reducing the favorable position taken from the development of security.
WEBSITE || WHITEPAPER || FACEBOOK || TWITTER || TELEGRAM ||
By Arsenyo
Комментарии
Отправить комментарий